How Quantum Computers Will Break Your Blockchain — And Why Tectonic Matters

As quantum computing becomes a technological reality, blockchain security faces unprecedented threats. Tectonic isn’t just surviving in the quantum era — it’s designed to thrive.
As quantum computing moves from theoretical milestone to technological reality, the blockchain industry faces a new class of threat. Post-quantum cryptography is not just a research topic anymore. It is a matter of survival.
Every major Layer 1 blockchain relies on classical cryptography that quantum machines are expected to break, but not all chains are equally vulnerable. This post is a practical field guide to understanding where each L1 is weakest and what a credible attacker would exploit first. We cover signature schemes, key exchange, wallet flows, and consensus systems to reveal the true surface area of risk.
Why Quantum Threats Matter
Quantum computers do not need to attack every part of a blockchain to cause damage. They only need to break the weakest link in the cryptographic chain. That may be a signature algorithm, a leaked public key, or a wallet recovery process.
With Shor’s algorithm poised to compromise elliptic curve cryptography, including ECDSA and EdDSA, nearly all digital assets become exposed. Quantum attacks will be able to:
- Forge digital signatures
- Spoof wallet recovery participants
- Decrypt archived encrypted data
- Intercept validator identities or tamper with consensus
The threat is not distant. It is already shaping the security roadmaps of national agencies and security-forward companies.
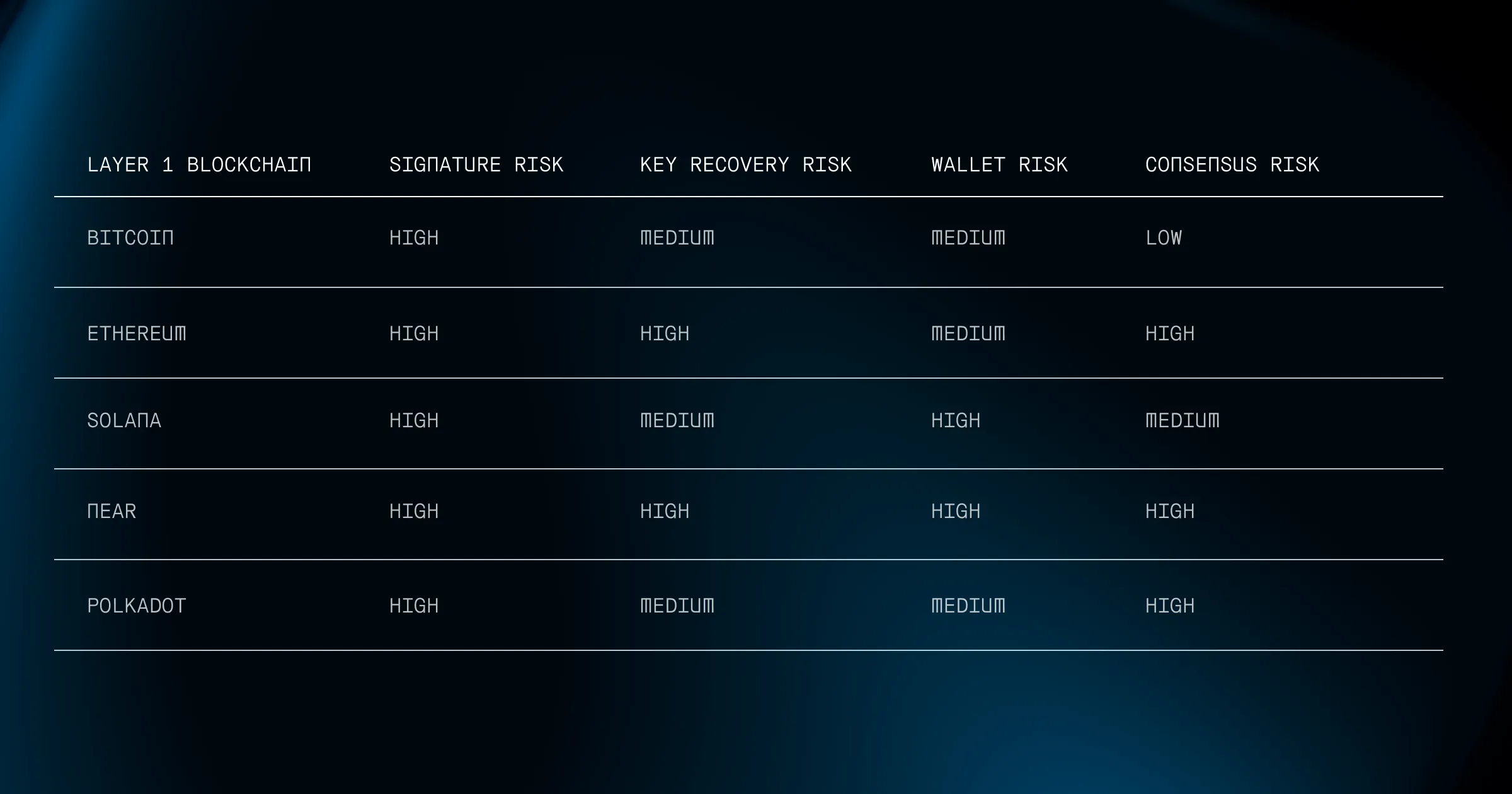
Where Layer 1s Are Most Exposed
We surveyed the most critical components across leading L1s to identify the areas with the highest quantum risk.
Signature Schemes
Most L1s use ECC-based signatures like ECDSA or Ed25519. These are directly broken by quantum computing.
- Ethereum: ECDSA
- Bitcoin: ECDSA
- Solana: Ed25519
Risk Level: Critical
Once a quantum computer can factor large integers (RSA) or compute discrete logs (ECC), it becomes possible to forge any previously seen signature. For Ethereum and Bitcoin, this is especially dangerous because public keys are often revealed after the first use.
Primary targets:
- Ethereum hot wallets
- Reused Bitcoin addresses
- Solana validators with static keys
Key Recovery and Exchange
Many chains use traditional key exchange protocols for encrypting messages and wallet recovery flows.
Risk Level: High
A quantum attacker could intercept and decrypt social recovery messages, threshold signatures, or multisig coordination flows if they are not protected by quantum-resistant mechanisms.
Notable vulnerabilities:
- Ethereum smart contract wallets with social recovery
- Multisig wallets
- Shared signing flows in MPC custodians
Wallet Infrastructure
Wallet libraries, APIs, and client software are some of the most neglected parts of the stack from a security standpoint.
Risk Level: Medium to High
Web-based and mobile wallets often leak metadata or reuse signature parameters. High-volume endpoints like wallets are natural entry points for adversaries.
Likely targets:
- Browser-based Ethereum wallets
- Mobile Solana wallets
- Aggregators that unify key management
Consensus Mechanisms
Consensus systems rely on signatures, randomness, and validator selection schemes. These are also vulnerable if based on classical assumptions.
Risk Level: Long-term critical
Proof-of-Stake validators and randomness beacons built using classical primitives will eventually be compromised. This is less immediate than signature-based risks, but the consequences are deeper once exploited.
At-risk systems:
- Ethereum’s BLS-based beacon chain
- Ethereum’s KZG commitment scheme for L2 blobs
- Polkadot’s BABE and GRANDPA
- Near’s VRF beacon
What A Quantum Attacker Would Target First
A rational quantum adversary will not try to break everything. They will start with the most valuable data that is the easiest to forge or decrypt. That includes:
- Cold wallets with on-chain public keys
- Reused Bitcoin addresses with visible keys
- Smart contract multisig wallets on Ethereum and Cosmos
- Validator identities on Solana and Near
- Archived bridge and DEX transaction logs
Many of these targets require no interaction with users. Once encrypted traffic or keys are harvested, it is just a matter of time until they are decrypted.
Heatmap Of Risk Across Layer 1s
No Patch Can Fix A Broken Foundation
Mitigating these risks is not about issuing a few software updates. A real fix means replacing broken primitives, rotating keys and certificates, updating every endpoint and client library, and rebuilding trust systems from scratch. It must be done while maintaining backward compatibility with chains and apps that have not migrated yet.
Tectonic is building blockchain infrastructure that is quantum-secure by default. Not patched, not forked. Designed from first principles for a post-quantum world.
Quantum threats do not arrive as a sudden collapse. They arrive as silent breaks in systems that were never meant to withstand them.
Most L1s are exposed. Many will not fix it in time. The ones that do will build the future on stronger ground.
Further Reading
- NIST Post-Quantum Cryptography Project
- Global Risk Institute: Quantum Threat Timeline
- Understanding Shor’s Algorithm